Just two days before Apple has disclosed a critical Security flaw in the SSL implementation on the iOS software that would allow man-in-the-middle attacks to intercept the SSL data by spoofing SSL servers.
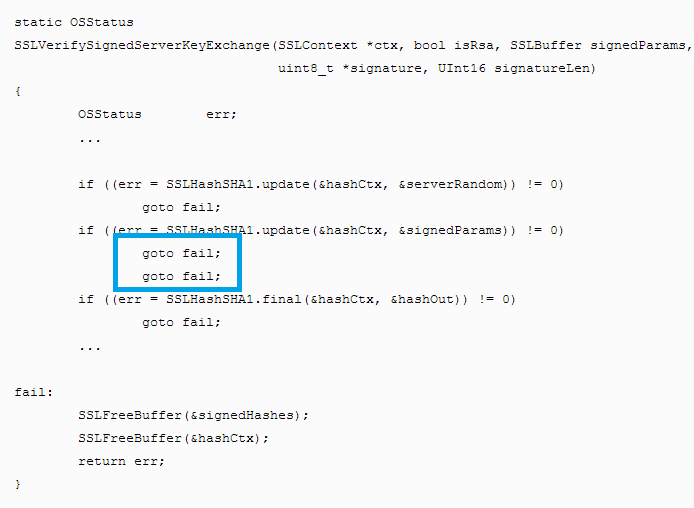
Dubbed as CVE-2014-1266, the so-called ‘goto fail;’ vulnerability in which the secure transport failed to validate the authenticity of the connection has left millions of Apple users vulnerable to Hackers and Spy Agencies, especially like the NSA.
Last Friday, Apple had also released updated version iOS 7.0.6 to patch the vulnerability, which was first discovered in Apple's iOS Devices, but later company had acknowledged its presence in Mac OSX also, that could allow hackers to intercept email and other communications that are meant to be encrypted in iPhone, iPad and Mac computer. Affected versions include iOS up to version 7.0.5 and OS X before 10.9.2.
Security Researchers confirmed, 'Nearly all encrypted traffic, including usernames, passwords, and even Apple app updates can be captured.' with man-in-the-middle attack.
Apple Vulnerability and NSA
I am sure; you still remember the NSA's DROPOUTJEEP Hacking Tool, implant for Apple iOS devices that allows the NSA to remotely control and monitor nearly all the features of an iPhone, including text messages, Geo-Location, microphone and the Camera.
DROPOUTJEEP program was developed in 2008 to conduct espionage on iPhone users, which was revealed by the documents provided by Edward Snowden a month ago. "The initial release of DROPOUTJEEP will focus on installing the implant via close access methods." document reads.
According to the vulnerability details published by a Google's Security Researcher 'Adam Langley', a basic mistake in a line of the SSL Encryption code almost screwed up the iOS SSL certificate verification process with an open invitation for the NSA's Prying Eyes.
"This sort of subtle bug deep in the code is a nightmare," Adam Langley said on his blog, "I believe that it's just a mistake, and I feel very bad for whoever might have slipped in an editor and created it."
Security researchers, Jacob Applebaum said last December, "Either the NSA has a huge collection of exploits that work against Apple products, meaning that they are hoarding information about critical systems that American companies produce and sabotaging them, or Apple sabotaged it themselves."
Although, those old techniques are no longer in circulation, but the NSA has a track record of continually evading the privacy of users by exploiting vulnerabilities in various softwares and obviously NSA's capabilities have improved significantly in the past five years.
In the DROPOUTJEEP document, the NSA also admitted, 'A remote installation capability will be pursued for a future release.' That means, it's practically possible that the NSA had already discovered this iOS SSL flaw in an effort to hack iPhone users' remotely by sniffing data and spoofing them to install malware.
An Unanswered Question
'Was the Apple intentionally injected backdoors for NSA or the flaw was an accident???' If it was an accident, then Apple would have been able to release patches for both iOS and Mac OS X at the same time, instead of releasing the patches for both, it silently released a fix for iOS devices on Friday night, but when the cryptographers and security experts began criticizing the company for leaving OS X without the patch, they finally acknowledged Mac OS X too; But it's the 4th day after disclosure and no patch yet has been released for Mac OS X.
Also, Apple contacted CVE (Common Vulnerabilities and Errors database) on 8th January 2014 to reserve the bug number CVE 2014-1266 for the SSL vulnerability and later they have released updated iOS 7.1, which was also vulnerable to the flaw that Apple had already discovered.
However, Apple categorically denied working with the NSA on a backdoor after it was accused last December of creating a way for the US intelligence agency NSA to access contacts and other data in iPhones.
On Dec. 31, Apple spokesperson released a statement saying:
"Apple has never worked with the NSA to create a backdoor in any of our products, including iPhone. Additionally, we have been unaware of this alleged NSA program targeting our products. Whenever we hear about attempts to undermine Apple's industry-leading security, we thoroughly investigate and take appropriate steps to protect our customers. We will continue to use our resources to stay ahead of malicious hackers and defend our customers from security attacks, regardless of who’s behind them."
In 2013, The US Department of Defense passed Apple's iOS 6 for the Government use, that means if the NSA was aware of this flaw, they didn't seem to have informed them.
To Check, whether your web browser is vulnerable to SSL flaw, Click here and to be safe, you are recommended to use an alternate web browser, rather than Safari web browser and avoid using public and unsecured networks.
UPDATE: Apple has finally today releases Mac OS X 10.9.2, which includes a fix for a major SSL security flaw and bringing with it a number of "improvements to the stability, compatibility and security of your Mac."
To Check, whether your web browser is vulnerable to SSL flaw, Click here and to be safe, you are recommended to use an alternate web browser, rather than Safari web browser and avoid using public and unsecured networks.
UPDATE: Apple has finally today releases Mac OS X 10.9.2, which includes a fix for a major SSL security flaw and bringing with it a number of "improvements to the stability, compatibility and security of your Mac."





Would love to here from you...