Several weeks ago we reviewed Incapsula, a Cloud-based Security service which can significantly enhance the security of your website, while also boosting its performance. Following this review we’ve received many responses from our readers who wanted to learn more about Incapsula protection services. Specifically, we were asked to explain more about Incapsula Enterprise plan features. To answer these questions, today we are going to take a look at Incapsula DDoS Protection services.
Distributed Denial of Service attacks
If your business has a web presence, chances are that you’ve already heard about Distributed Denial of Service attacks. In case you didn’t, a Distributed Denial of Service (DDoS) attack is a DoS attack that is usually carried out by a “botnet”, a network of computers acting in concert to overwhelm the server by depleting all available resources.
Recently we all witnessed a large DDos attacks on U.S. banks by Muslim hacker group, an attack which crippled the site, effectively cutting all bank customers from using online services for extended periods of time. In the recent years, such attacks are becoming more and more common and are now targeting even small and medium online business, as well as big and prominent websites.
Just like in HSBC attack, a typical size DDoS can bring down a website and even crush an entire network of servers. Moreover, because it relies on size and brute force rather than on existence of vulnerabilities, DDoS is very hard to prevent and to mitigate. Currently, the only true DDoS protection can be provided by reliable user-identification techniques and by strong server infrastructure.
Incapsula – Complete DDoS Protection
Incapsula DDoS Protection service use both defense techniques, by integrating a Global network of multi-gigabit scrubbing centers with a unique bot (automation) detection technology.
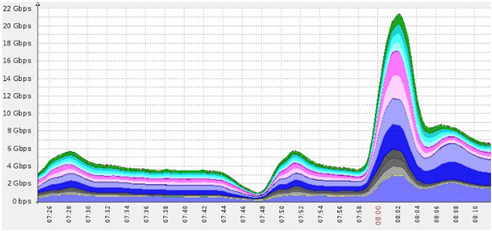
As a result, Incapsula provides complete protection from network (Layer 3 & 4) and application level (Layer 7) DDoS attacks. The effectiveness of Incapsula is clearly demonstrated by the screenshot above which shows the successful mitigation of an escalating DDoS attack. The attacks lasted for an more than an hour and peaked at a destructive 22Gbs volume. As evident from the image above, Incpaula’s network handled this attack well, coming out of it with all of its servers 100% active for 100% of the time.
The other end of this scenario reveal itself in this quote from one of Incapsula’s customers: Witold Radomski, a CTO of the very popular Enjin.com.
In the Enjin case study published on Incapsula site Witold says this:
“Our network was finally clear from the endless onslaught of crippling UDP & SYN flood attacks. Using Incapsula's dashboard, we were able to see exactly when each attack was happening, and continue delivering service to millions of users during the attack. We also saw a sharp drop in unwanted bot activity, which resulted in a 20% drop in load on our servers.
A key feature we were looking for is a very low false positive rate during mitigation. Incapsula proved to have a near zero false positive rate, and legitimate users had no trouble accessing Enjin websites during prolonged DDOS attacks.”
The second part of this quote is especially revealing as it points to one of Incapsula main strengths. Namely, it’s accurate and un-hindering visitor identification algorithm.
Zero Business Disruption
In addition to the sheer strength and scalability of its network, Incapsula’s other advantage is in the way it performs during the attack. When hit by DDoS, most mitigation services will apply intrusive challenges to website visitors (such as a CAPTCHA, or delay pages) to compensate for the lack of better identification techniques. Of course, such challenges are not a valid option for most commercial sites, they will drive away human visitors who detest such CAPTCHAs and delays.
Recognizing that, Incapsula implements smart identification algorithms that can provide the same level of protection while working seamlessly in the background and allowing immediate access to human visitors, even during the attack. This also deals with another inherent limitation of CAPTCHA and JS challenges, which are not always effective when it comes to direct access to website resources (i.e. downloading an image).
So how does Incapsula identify non-human DDoS agent? I found that Incapsula generally have three types of identification methods, listed in descending preference:
1. Verified Clients: This group includes humans with strong classification characteristics, according to Incapsula Client Profiling. Here you will also verified non-human entities such as search engines and website monitoring tools. This is basically how Incapsula leverages its accumulated knowledge for quick and accurate identification.
2. Challenges and Obstacles: If the visitor is not verifiable the visit will have to undergo a challenge. Challenges are intended to provide the visitor with an opportunity for redemption and are mostly performed seamlessly, with minimal effect on the actual session.
3. Heuristic and Statistical methods Statistical anomalies: By monitoring statistical data, like client requests rate and clustering, the system can identify the most problematic site visitor populations (such as Web Browser that have their cookie support turned off). During DDoS the access rate for these populations will be limited, to provide better support for verified visitors.
Sounds interesting? It should, because by combining strong infrastructure with smart identification algorithms, Incapsula offers complete defense against all types of DDoS threats, including network-based attacks (like SYN or UDP floods) and application attacks that attempt to overwhelm server resources. Of course the service will also block attacks that try exploit application and web server vulnerabilities, like Slowloris.
For more information about Incapsula you can visit: www.incapsula.com




Would love to here from you...