Tor is one of the best and freely available privacy software that
lets people communicate anonymously online through a series of nodes
that is designed to provide anonymity for users and bypass Internet censorship.
When you use the Tor software, your IP address remains hidden and it
appears that your connection is coming from the IP address of a Tor exit relay or nodes,
which can be anywhere in the world. An exit relay is the final relay
that Tor traffic passes through before it reaches its destination.
According to a recent report 'Spoiled Onions: Exposing Malicious Tor Exit Relays', published by security researchers Phillip Winter and Stefan Lindskog revealed that almost 20 exit relays in the Tor anonymity network that attempted to spy on users’ encrypted traffic using man-in-the-middle techniques.

Both Researchers spent more than four months studying on the Tor exit nodes using their own scanning software called "exitmap"
and detected suspicious behavior somewhere in Russian network. They
identified 25 nodes that were tampering the web traffic and stripping
out the encryption using 'sslstrip' attack.
They found some faulty nodes, may be because of configuration errors or
ISP issues, but 19 nodes were caught using a bogus SSL certificate to
perform man-in-the-middle attacks on users. Those buggy nodes were
programmed to intercept only traffic to the Facebook website.
”I’m not even sure if they captured passwords,” the researcher said. “Maybe it was just an experiment. It didn’t seem like a very sophisticated and serious attack to us.”
”I’m not even sure if they captured passwords,” the researcher said. “Maybe it was just an experiment. It didn’t seem like a very sophisticated and serious attack to us.”
In a blog post on Tor Project website, the author described that:
"First, it's important to understand that 25 relays in four months isn't a lot. It is ultimately a very small fraction of the Tor network. Also, it doesn't mean that 25 out of 1,000 relays are malicious or misconfigured (we weren't very clear on that in the paper)."
"Even if your traffic is going through a malicious exit relay, it doesn't mean that everything is lost."
They also noticed that the Russian nodes were re-encrypting the traffic
with their own self-signed digital certificate issued to the made-up
entity Main Authority.
"Finally, we want to point out that all of these attacks are of course not limited to the Tor network. You face the very same risks when you are connected to any public WiFi network. One of the fundamental problems is the broken CA system."
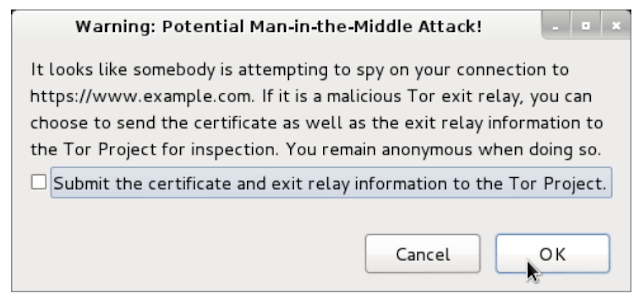 In conclusion, they have also released a patch for the issue as a browser extension called "Torbutton"
that informs users when a man-in-the-middle attack is potentially in
progress and offers the option to send an anonymous report to the Tor
Project.
In conclusion, they have also released a patch for the issue as a browser extension called "Torbutton"
that informs users when a man-in-the-middle attack is potentially in
progress and offers the option to send an anonymous report to the Tor
Project.
"We developed a set of patches for the Tor Browser Bundle, which is capable of fetching self-signed X.509 certificates over different network paths to evaluate their trustworthiness."
The Exit Relay Scanning tool "exitmap" is freely available and written in pure Python language. You can download it from GitHub.




Would love to here from you...